Architecture
The following figure shows the WEL architecture using DCAS and RACF® as the example host credential mapper.
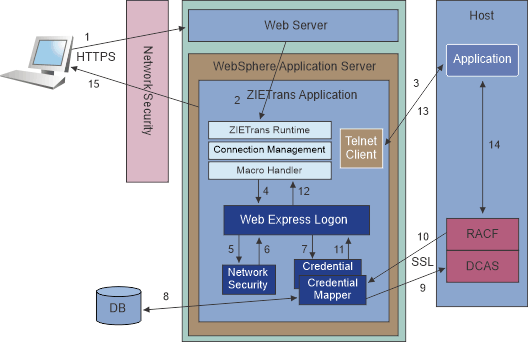
- The user submits a request to connect to a ZIETrans application
through a Network Security Application (NSA).
The NSA authenticates the user using either an X.509 certificate or a user ID and password. After authentication the NSA authorizes access to the requested application based on policy information associated with the user. The NSA then passes the user's network credentials (network ID) through the Web server to the WebSphere® Application Sever.
IBM® Tivoli® Access Manager is an example of an NSA.
- WebSphere Application Server routes the request to ZIETrans.
- The ZIETrans runtime starts a Telnet connection to the host.
- The ZIETrans macro handler runs the WEL logon macro. See How to create a WEL logon macro. WEL receives a Java™ function call from the macro requesting that host credentials (host user ID and password or passticket) be returned.
- WEL calls the appropriate Network Security plug-in to retrieve
the user's network ID from where it was saved by the NSA.
You must configure to ZIETrans the Network Security plug-in that corresponds with the NSA being used. See Network Security plug-in.
- The Network Security plug-in returns the user's network ID.
- WEL calls the appropriate Credential Mapper plug-in to
convert the user's network ID and host application ID to host
credentials (host user ID and password or passticket).
You must configure to ZIETrans the Credential Mapper plug-ins that correspond with the credential mappers being used. See Credential Mapper plug-ins.
- The Credential Mapper plug-in calls a function (in this case, a JDBC-accessible database such as
IBM
DB2®) to map the user's network ID to a host user ID.
The Credential Mapper plug-ins provided with ZIETrans are designed to use a JDBC-accessible database. Another possibility is to use an LDAP directory. However, if you use LDAP, you must create your own custom plug-in. For more information see the chapter, Creating plug-ins for Web Express Logon.
- The Credential Mapper plug-in calls the back-end credential mapper (in this case DCAS and RACF) with the host user ID and host application ID and requests a passticket.
- RACF generates and returns a passticket.
- The Credential Mapper plug-in returns the host user ID and passticket to WEL.
- WEL returns the host user ID and passticket to the macro.
- The macro inserts the host user ID and passticket onto the host logon screen.
- The host application verifies the host user ID and passticket and allows the connection.
- The host application screen is presented to the user.